Introduction
SQL injection attacks are one of the most common types of cyber attacks that target web applications. In a SQL injection attack, malicious code is inserted into a database query through a vulnerable entry point in the application. This allows attackers to gain access to sensitive data or even take control of the entire database. Java applications are particularly vulnerable to SQL injection attacks, as Java is a widely used language for building web applications. In this article, we will discuss some best practices that can be implemented to prevent SQL injection in Java applications.
What Is Java SQL Injection?
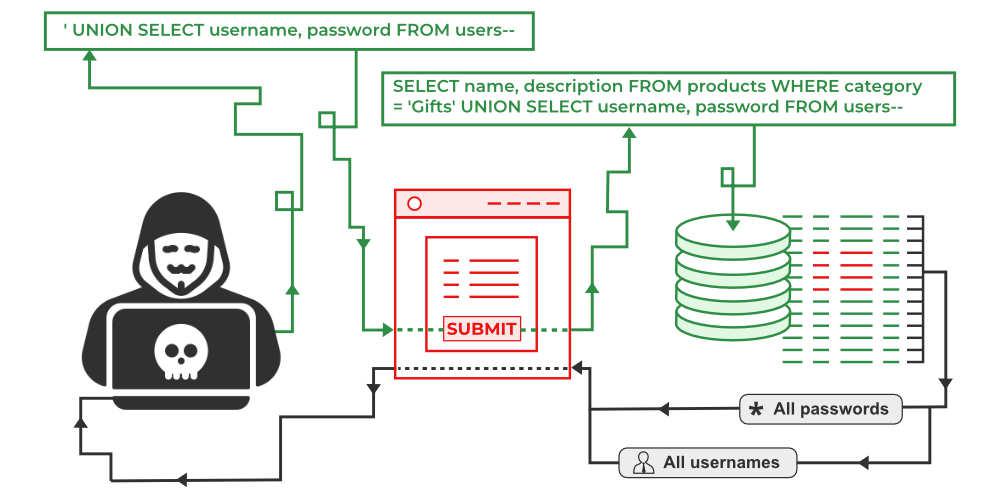
Technically, there is no such thing as a “Java SQL injection.” When we say that, we’re just referring to SQL injection attacks on Java codebases. The question then becomes, “What is SQL injection?”
SQL injection is a type of cybersecurity attack that occurs when an attacker is able to insert or manipulate malicious SQL (Structured Query Language) statements within an application’s query. This is typically achieved by exploiting vulnerabilities in the application’s input validation mechanisms. SQL Injection stands as one of the most prominent vulnerabilities in web applications, consistently ranking among the top 10. This vulnerability is pervasive and can manifest in various applications utilizing relational databases such as Oracle, MySQL, PostgreSQL, and SQL Server.
To carry out SQL Injection, a malicious user begins by searching for a place in the application where he may inject SQL code with data, which could occur within a SQL Compiler. It might be the login page for a web application or anywhere else. As a result, when the application receives data embedded with SQL code, the SQL code will be performed along with the application query.
SQL Injection: A Basic Example
Consider the following line of code:
String pass = "12345"; // this would come from the userString query = "SELECT * from users where name = 'USER' " + " and password = '" + pass + "'";At first glance, this code may not raise immediate concerns. However, imagine a scenario where a user enters the following string as their password:
'; DROP TABLE users --In the concatenation process, the quote at the beginning seamlessly integrates with the existing one in the query. Additionally, the two dashes at the end signify that any data following them will be recognized as comments. Therefore, the final query would appear as such:
SELECT * from users where name = 'USER' and password = ''; DROP TABLE users --'Instead of Selecting a user, we would be dropping the entire table!
While this example may appear extreme, it underscores the risk of SQL injection. For this attack to succeed, the attacker must possess knowledge about the table’s name (in this case, ‘users’), and they might use another type of SQL injection to gather such information. Additionally, the database connection employed in this part of the application must have privileges to execute a ‘DROP TABLE’ operation—a practice strongly discouraged for security reasons.
Types of SQL Injection
Generally, there are four SQL injection types:
1. Boolean-Based SQL Injection
The earlier example illustrates a case of Boolean-Based SQL Injection, employing a boolean expression that evaluates to true or false. This method is utilized to extract additional information from the database. For instance:
Input Data: 2 or 1=1SQL Query: SELECT first_name, last_name FROM tbl_employee WHERE empId=2 OR 1=1By crafting the input as above, an attacker can manipulate the query to reveal more information.
2. Union-Based SQL Injection
The Union-Based SQL Injection leverages the SQL union operator, which combines data from two distinct queries with the same number of columns. This technique is employed to retrieve data from other tables. For example:
Input Data: 2 UNION SELECT username, password FROM tbluserQuery: SELECT first_name, last_name FROM tbl_employee WHERE empId=2 UNION SELECT username, password FROM tbluserThis form of SQL injection can be exploited to obtain sensitive user credentials.
3. Time-Based SQL Injection
Time-Based SQL Injection involves injecting special functions into the query that can pause execution for a specified duration. This attack can significantly impact database server performance and potentially lead to application downtime. For instance, in MySQL:
Input Data: 2 + SLEEP(5)Query: SELECT emp_id, first_name, last_name FROM tbl_employee WHERE empId=2 + SLEEP(5)The query execution in this example would pause for 5 seconds.
4. Error-Based SQL Injection
Error-based SQL Injection relies on injecting SQL that is intentionally syntactically incorrect, prompting the database server to return error codes and messages. Attackers can exploit this information to glean details about the database and system.
How To Prevent Java SQL Injections
Now, let’s discuss SQL Table Creation and its relevance in preventing SQL injection.
1. Input Validation
Input validation is another important practice that can help prevent SQL injection in Java applications. By validating user input data and ensuring that it conforms to the expected format, you can prevent malicious input from being injected into a database query. One approach to input validation could be developing a custom validation framework according to your application needs.
2. Use Prepared Statements and Parameterized Queries
One of the fundamental practices to prevent SQL injection is to utilize prepared statements and parameterized queries. Prepared statements automatically handle the escaping and sanitization of user inputs, making it difficult for attackers to inject malicious code. Here’s an example using JDBC:
String sql = "SELECT * FROM users WHERE username = ? AND password = ?";try (PreparedStatement statement = connection.prepareStatement(sql)) { statement.setString(1, enteredUsername); statement.setString(2, enteredPassword); ResultSet resultSet = statement.executeQuery(); // Process the result set} catch (SQLException e) { // Handle exceptions}3. Avoid Dynamic SQL Queries
It’s advisable to refrain from creating SQL queries dynamically through string concatenation, particularly when working with user input. If it’s necessary to use dynamic queries, it is crucial to perform appropriate validation and sanitization of any user input to minimize the likelihood of a SQL injection attack.
4. Implement Principle of Least Privilege
A very effective way to prevent SQL injection attacks is to implement the principle of least privilege. This simply means to allocate the minimum amount of privileges that a user requires to execute a particular task. For instance, if a user only requires permission to read from a specified database, then you should grant read-only access to that user. In the event of a SQL injection attack, the attacker will only have access to data the user has been granted access to.
5. Web Application Firewall (WAF)
Consider using a Web Application Firewall to add an additional layer of defense against SQL injection attacks. WAFs can detect and block malicious SQL injection attempts, enhancing the overall security of your application.
6. Security Code Reviews
Regularly perform thorough security code reviews to ensure that all developers are knowledgeable about and adhere to the best practices for preventing SQL injection. Proactively address any vulnerabilities that are identified and encourage a development culture that prioritizes security.
Conclusion
To ensure the security and integrity of Java applications that interact with databases, it is crucial to prioritize the prevention of SQL injection. By implementing the best practices mentioned above, developers can significantly mitigate the risk of SQL injection vulnerabilities and safeguard sensitive data from malicious exploitation. It is important to consistently update security measures, stay informed about emerging threats, and conduct comprehensive security audits to maintain a strong defense against SQL injection attacks.
FAQs
Ans: SQL injection is a type of cyber attack where malicious SQL code is injected into a query through user-inputted data, posing a significant threat to the security of Java applications interacting with databases. We can avoid it by following the steps, underlined in the article.
Ans: SQL injection can lead to unauthorized access, data manipulation, or even data deletion. It exploits vulnerabilities in input validation, allowing attackers to execute arbitrary SQL commands, compromising the integrity and confidentiality of the application’s data.
Ans: A Web Application Firewall (WAF) adds an extra layer of defense by detecting and blocking SQL injection attempts. It acts as a barrier between the application and the internet, helping filter out potentially malicious SQL code.
Read Some Latest Blogs
- Data Science vs Data Analytics: Top Key Differences for Success

- How To Become A Data Scientist In India?: Achieve Your Data Scientist Dreams

- What are Callback Function in JavaScript?: A Guide to Effective Implementation

- Top 9 Interview Questions and Answers for Freshers Success

- What Is Python and Its Dynamic Uses?


